 Dictionary meaning of Eavesdropping– “Eavesdropping is secretly listening to the private conversation of others without their consent.”
Dictionary meaning of Eavesdropping– “Eavesdropping is secretly listening to the private conversation of others without their consent.”
Planting a bug (Audio Transmitter or a phone tapping device) to listen to your private conversations and using the same to steal data or information and corporate espionage also come in eavesdropping category.
However there are much smarter ways to listen to your private conversation than the traditional tapping of phone lines. You might not even know that who is listening to your conversation and using the same for their personal benefits causing loss to you and your business.
Anyone can plant an electronic bug to eavesdrop on your conversations and use them for stealing tenders, using critical information and stealing all your business moves and hence causing you and your business a damage that might affect you for a very long time.
How to deal with it? – Eavesdropping Detection Solutions
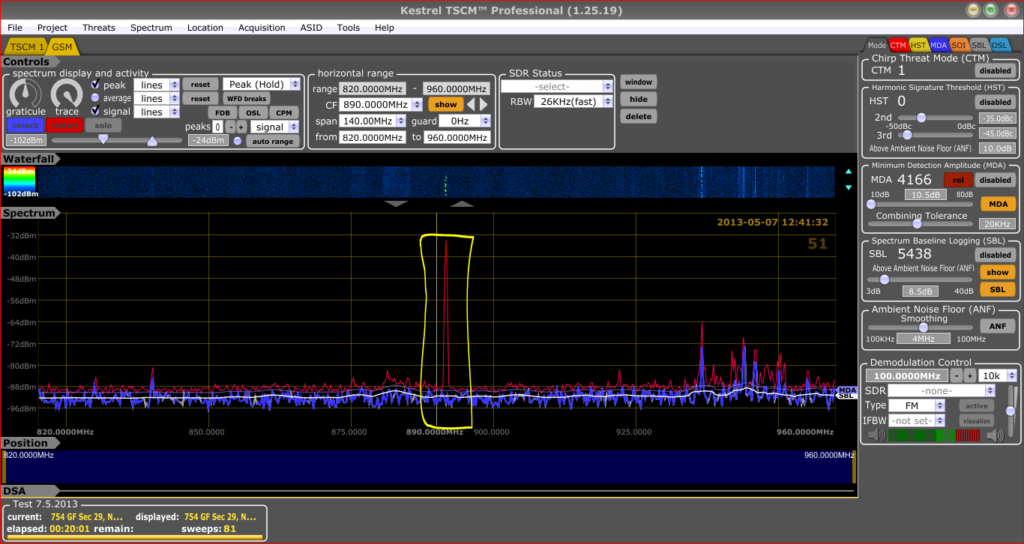
Fortunately there are ways. TSCM experts like AV2 Group are equipped with highly sophisticated Eavesdropping Detection equipment, also known as Technical Surveillance Countermeasures (TSCM) equipment, which can sweep your facility for electronic bugs (debugging services) and hence make your facility a safe place again.
Send us your query using the button below or write to us at info@av2group.net or av2group@gmail.com or call us at 0120 – 431 7823 or +919810635360 to get top quality Eavesdropping Detection Services by highly trained and certified debugging experts. Please remember not to call us from your phone or your mail ID or from your facility requiring our services. We understand that your business information is critical for you and needs to be protected.




 What is debugging or bugs sweep or Counter Surveillance Services? These are different names for TSCM services (Technical Surveillance Counter Measures) which actually is sweeping your facility for electronic bugs using highly sophisticated equipment.
What is debugging or bugs sweep or Counter Surveillance Services? These are different names for TSCM services (Technical Surveillance Counter Measures) which actually is sweeping your facility for electronic bugs using highly sophisticated equipment.
 Are Your Conference Rooms Safe? Make it happen by TSCM debugging Services
Are Your Conference Rooms Safe? Make it happen by TSCM debugging Services




 Tapping of telephone is a very common practice for data theft. Bugs in telephone is generally placed by a virus & using this your sensitive data & classified business information can be at risk.
Tapping of telephone is a very common practice for data theft. Bugs in telephone is generally placed by a virus & using this your sensitive data & classified business information can be at risk.